
I had to troubleshoot an issue and started with logs. Since we are in Azure PaaS, I used Kudu or App Service Explorer to search for recent logs. It was absolutely time-consuming.
AzureTools comes to the rescue. It is a simple .aspx page that can be dropped into CM environments, and download logs in seconds.
https://support.sitecore.com/kb?id=kb_article_view&sysparm_article=KB0420753
Download the recent AzureTools-1.2.0 (It should work with any Sitecore version) –
Unzip and drop the AzureTools.aspx in https://[CM_Site]/sitecore/admin folder
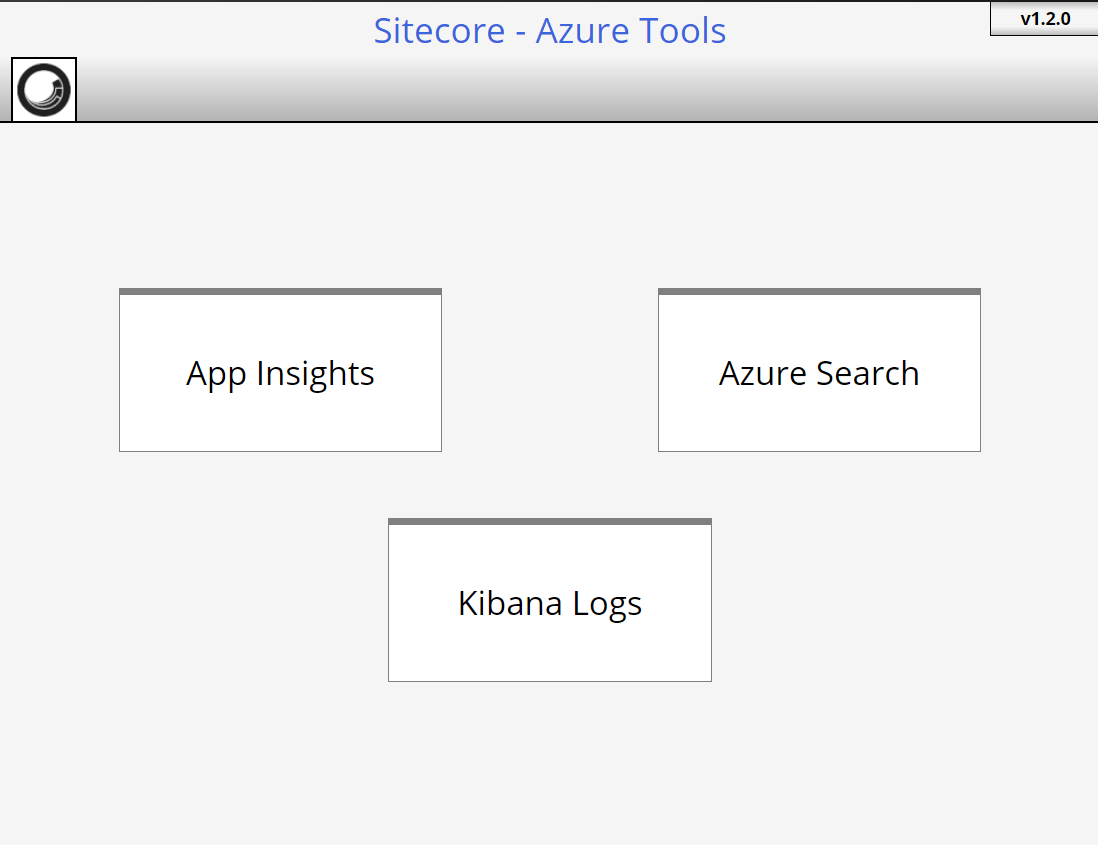
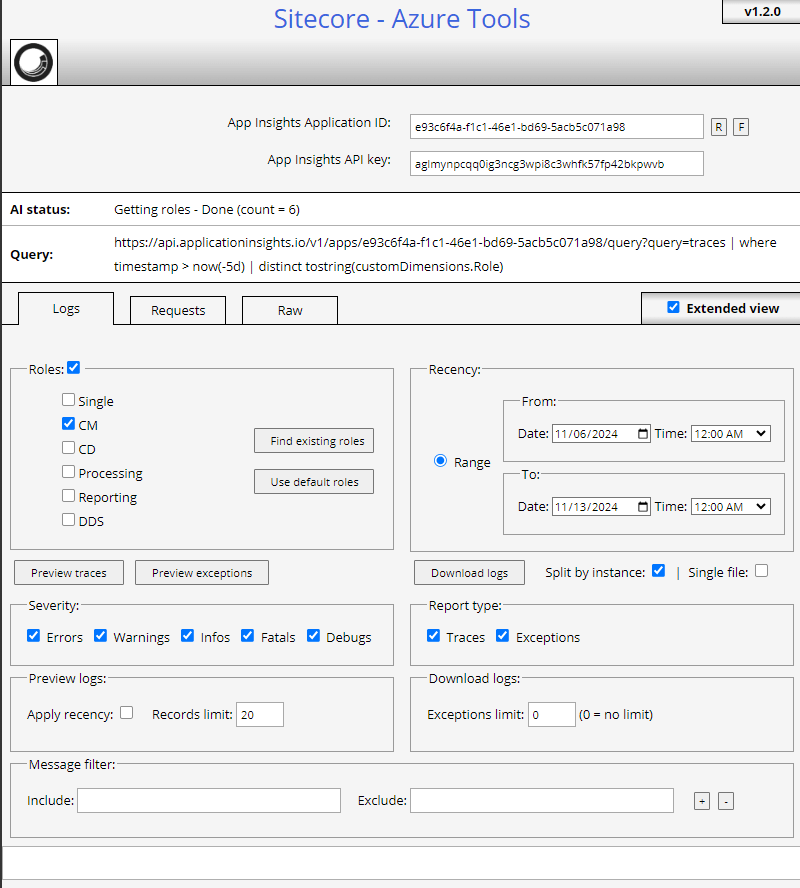
Now it’s ready to download logs from App Insights, Azure Search, and Kibana Logs – https://[CM_Site]/sitecore/admin/azuretools.aspx
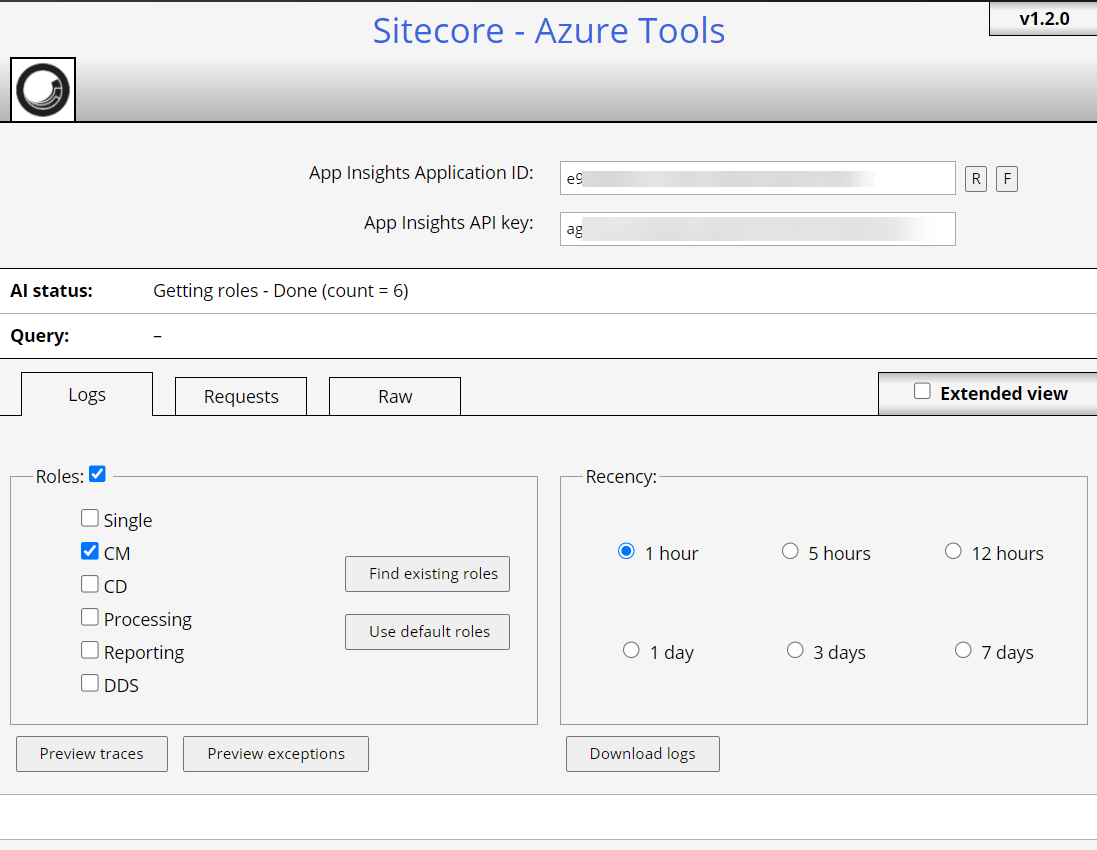
To pull logs from App Insights, need the Application ID and API Key.
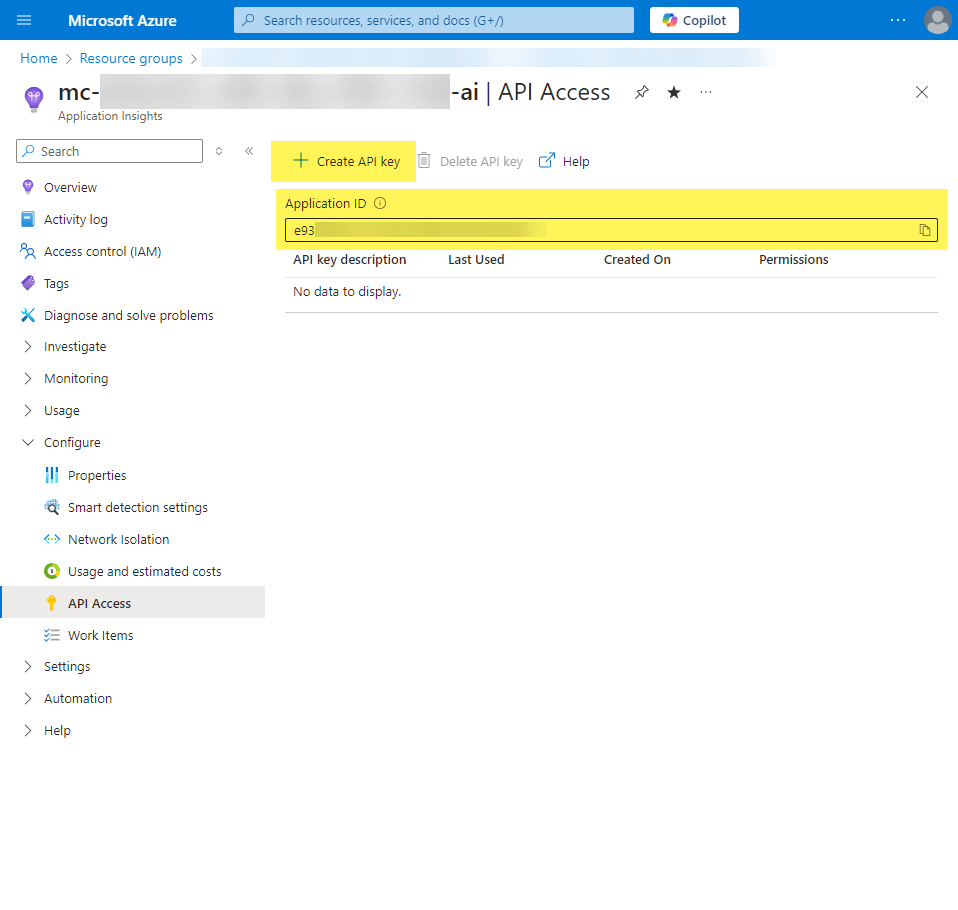
Application ID:
Navigate to the Azure App Insights Resource -> Configure -> API Access.
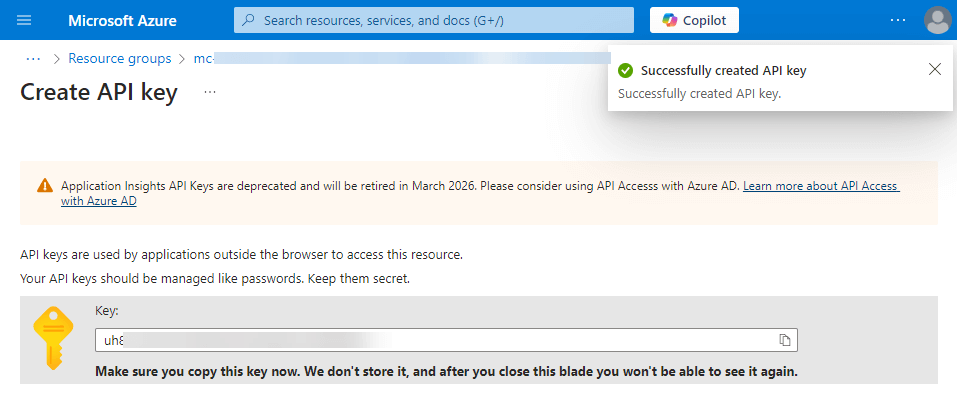
 API Key:
API Key:
– Create the API Key with Read Telemetry access.
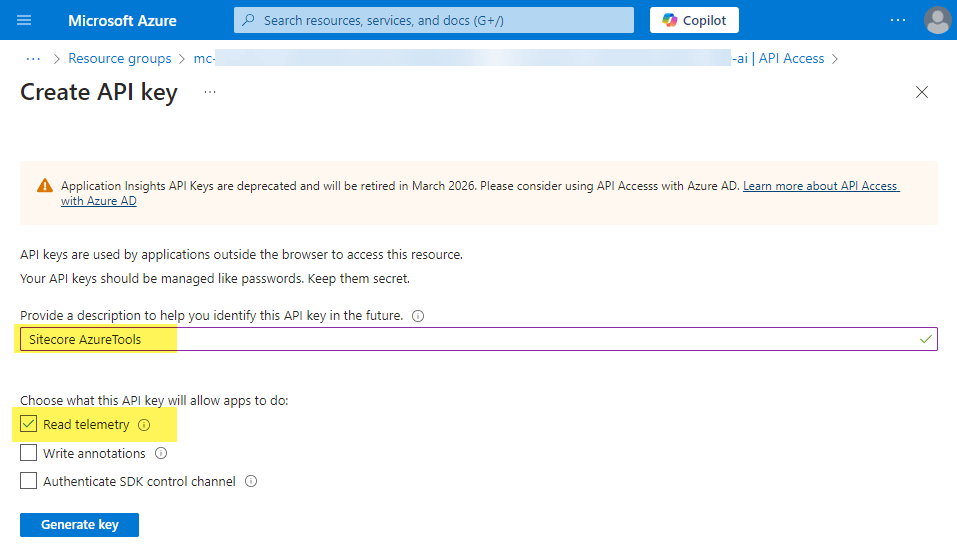
Remember to save the key in notes, you can’t get it after creation!
Now I was excited to download logs –
But then it’s erroring out –
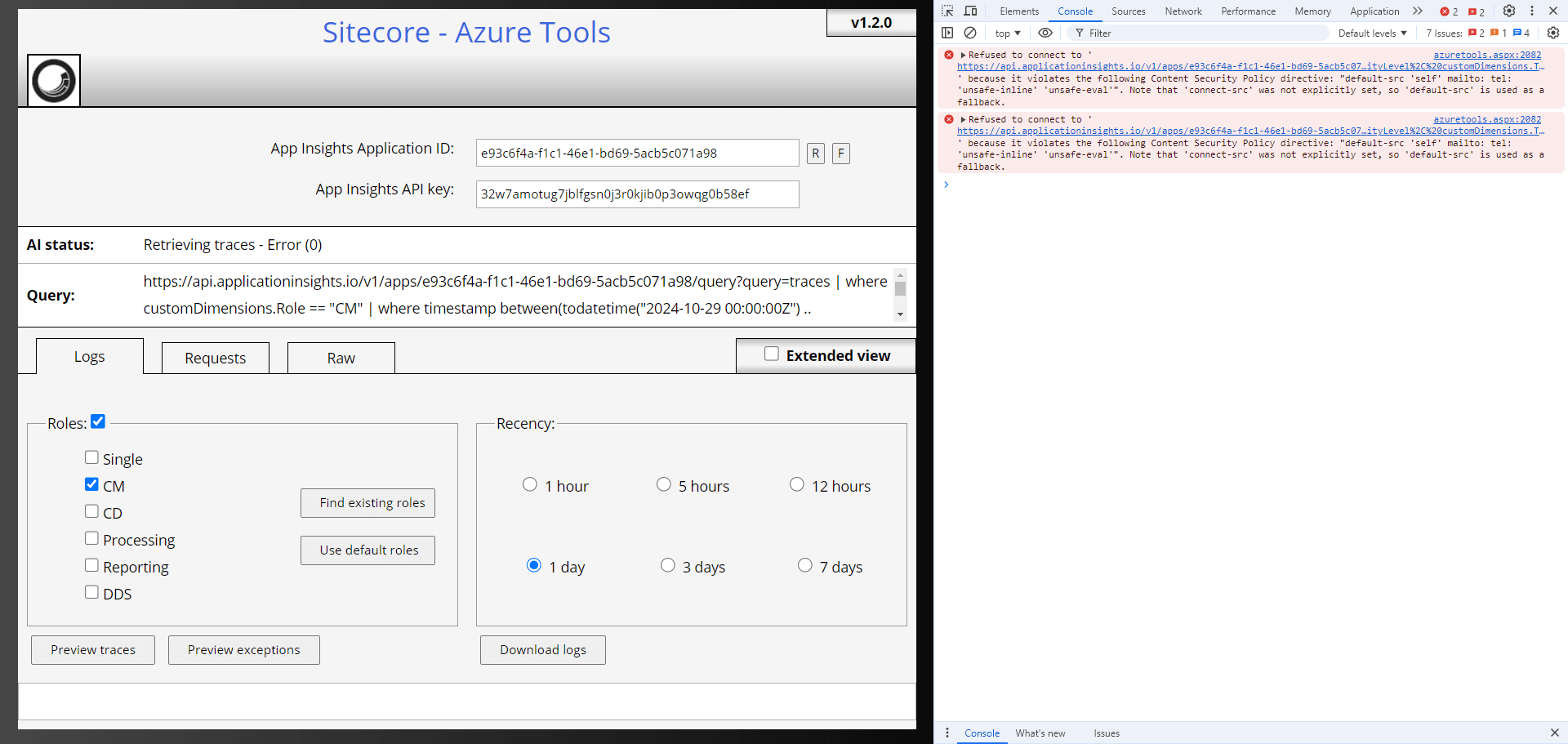
The console is showing the following error –
azuretools.aspx:2082 Refused to connect to ‘https://api.applicationinsights.io/v1/apps/e…ityLevel%2C%20customDimensions.ThreadName%2C%20customDimensions.StackTrace’ because it violates the following Content Security Policy directive: “default-src ‘self’ mailto: tel: ‘unsafe-inline’ ‘unsafe-eval'”. Note that ‘connect-src’ was not explicitly set, so ‘default-src’ is used as a fallback.
It made me curious to check the Web.Config – I couldn’t find the content-src node, added the following line.
connect-src ‘self’ ‘unsafe-inline’ ‘unsafe-eval’ https://api.applicationinsights.io;
<location path="sitecore"><system.webServer><httpProtocol><customHeaders><!--Adding mailto: and tel: which are currently blocked in iframes. Seems like a Chrome bug that never got fixed: https://bugs.chromium.org/p/chromium/issues/detail?id=663325 --><add name="Content-Security-Policy"xdt:Locator="Match(name)"xdt:Transform="SetAttributes"value="default-src 'self' mailto: tel: 'unsafe-inline' 'unsafe-eval'; img-src 'self' data:; style-src 'self' 'unsafe-inline' https://fonts.googleapis.com; font-src 'self' 'unsafe-inline' https://fonts.gstatic.com; upgrade-insecure-requests; block-all-mixed-content;"/>value="default-src 'self' mailto: tel: 'unsafe-inline' 'unsafe-eval'; img-src 'self' data:; style-src 'self' 'unsafe-inline' https://fonts.googleapis.com; font-src 'self' 'unsafe-inline' https://fonts.gstatic.com; connect-src 'self' 'unsafe-inline' 'unsafe-eval' https://api.applicationinsights.io; upgrade-insecure-requests; block-all-mixed-content;"/></customHeaders></httpProtocol></system.webServer></location>
Now I’m able to pull logs, preview traces, and exceptions.
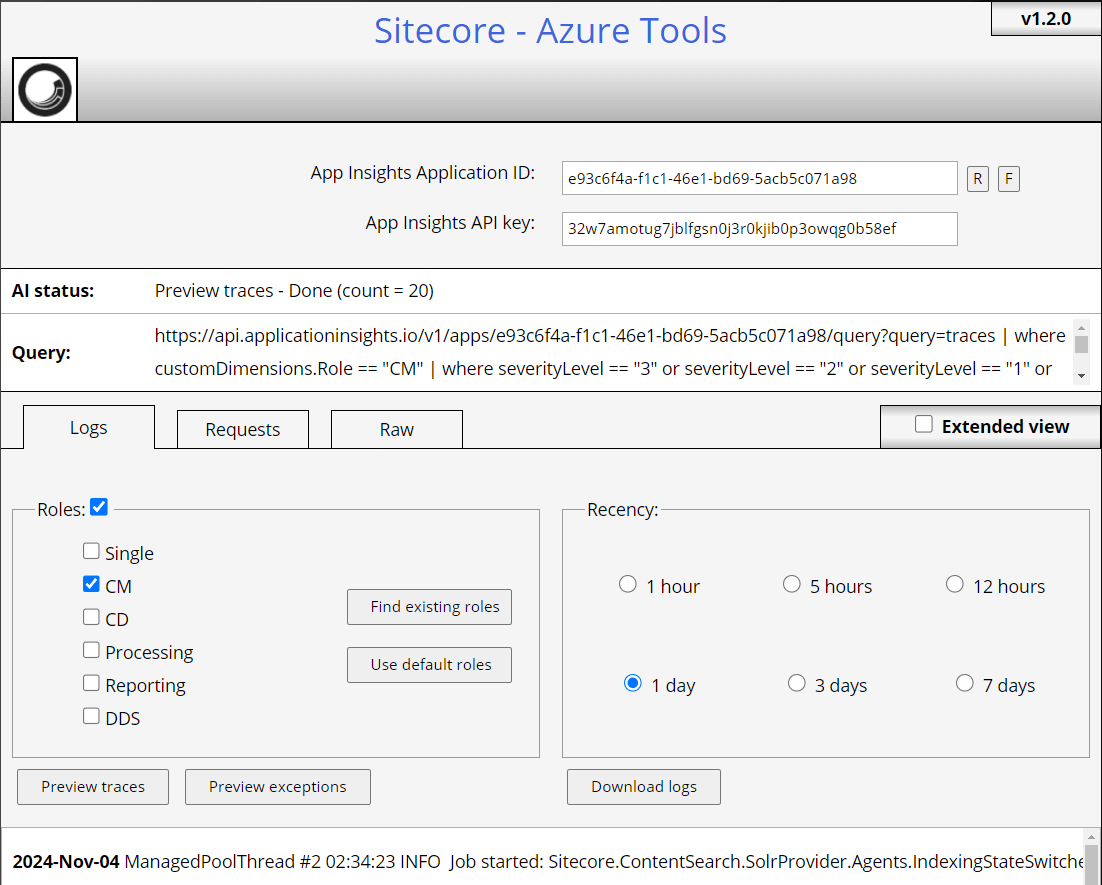
Utilize the Extended View for more filtered options.
Hope it helps.
Happy Sitecoring!








